Get familiar with DNS Hijacking
Hello mates, it has been a while since I publish my last blog. I am really happy that you took out your time to read this blog and I hope you are fine as well. So, few weeks earlier, I learned a technique from a friend of mine (which you will eventually see later soon in this blog) and thought that why shouldn’t I wrote a blog on this technique/attack, whatever you might call this, for myself? So I finally wrote one. I hope you enjoy.

Contents of this blogs will be:
- What is DNS?
- DNS Attacks
- DNS Hijacking (the main part!)
- Mitigations
Let’s jump in!
What is DNS?
Having to remember these IP address of every major websites like google, microsoft and amazon can be real difficult and nearly impossible to learn all of the websites we like. To overcome this difficulty, DNS servers came into existence. DNS or Domain Name System resolves human readable domain name like example.com to a computer readable IP address x.x.x.x. Have a look at DNS in detail by cloudflare.
You can find a list of public DNS servers here.
Let us see how we can perform a query to domain name, example.com using a tool called, nslookup is a command line tool to query Internet domain name servers. By default, nslookup will our DNS settings but you can override it using the “server” command.
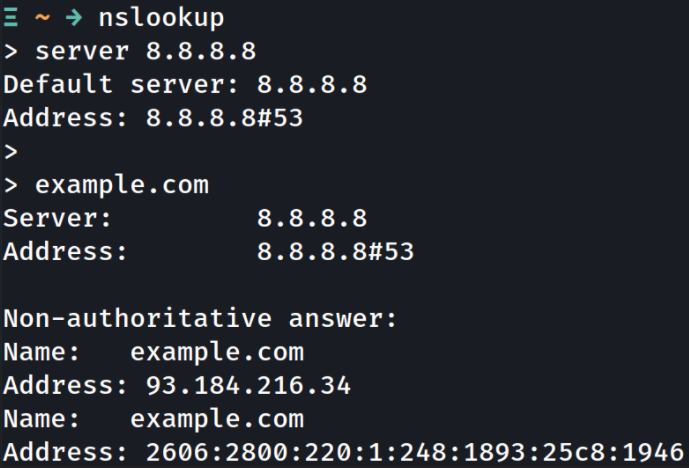
We can see that after setting DNS server to 8.8.8.8 (Google’s public DNS server), we query the example.com which gets resolved to IPv4 address 93.184.216.34 and to a long IPv6 address which I’m … super lazy to write!
Okay, so this was basics of DNS, but what’s wrong with it? Well, the problems lies here….
DNS Attacks
As we know that DNS servers are used for resolving human readable domain names to the numbers which computer understands. And, what do you think something can go possibly worse? A DNS attack…
DNS can be attacked by hackers through various vulnerabilities:
- DNS Hijacking
- DoS
- DNS amplifications
Alright, so question is what can possibly go worse with these attacks?
Let’s see DNS Hijacking in detail!!
DNS Hijacking
DNS Hijacking, also referred to as DNS redirection, is the process utilized by hackers to alter resolution of DNS using the malware. When users visit hijacked website, they’re redirected to an illegitimate website which looks alike the original website.

Please don’t confuse it with DNS Spoofing. Although, these two terms might look similar but has difference. Refer this article of Most Popular Types of DNS Attacks for more information.
Actually there is a file in Linux /etc/resolve.conf which is responsible for conversion of domain names into IP address. This process is called resolving.
There is another file in Linux /etc/hosts, which is responsible for translating/mapping arbitrary hostnames to arbitrary IP address, which can be used for testing on local environment.
But don’t get confused between both — resolv.conf file is used for dns resolution and hosts file is used for static resolution. Read here for more!
Let’s try to visit example.com and we are presented with webpage,

What actually happened in the backend is that when we typed out example.com, the browser will first check the local cache and see if there is any cached data exist regarding website. If it does, then browser will simply load the website and present it for us. But if it doesn’t, then browser will query local name server and so on and so forth unless it finds the IP address corresponding to domain name. We can actually Hijack this DNS server. Let’s see.
Now, I will demonstrate how you can hijack DNS with dnschef tool.
DNSChef is a highly configurable DNS proxy for Penetration Testers and Malware Analysts. A DNS proxy (aka “Fake DNS”) is a tool used for application network traffic analysis among other uses. For example, a DNS proxy can be used to fake requests for “badguy.com” to point to a local machine for termination or interception instead of a real host somewhere on the Internet.
First we will check our kali machine’s IP address using ip a show <interface> command,
ip a show eth0
Next, we check the IP address of the nameserver from /etc/resolv.conf file,
cat /etc/resolv.conf
we can change the IP address of the nameserver and point is to our IP address (kali machine) so that whenever we issue a request to the domain name, the resource will be provided as our resource.
I have changed the nameserver IP address with my kali machine IP address. You need to be privileged user in order to make changes to /etc/resolv.conf file,
sudo nano /etc/resolv.conf
cat /etc/resolv.conf
Now, let’s make an index.html file to serve as resource when we browse the domain in our browser,
cat index.html
Now, we actually need to host this file so that when request is made to any domain, this index.html file gets fetched from our system. And we can achieve this using python server,
python3 -m http.server 80 #we need to set port as 80 because by default python server run on port 8080
Now, let’s trigger the boss, dnschef by providing domain name, ip address to fake and an interface,
dnschef — fakedomains=example.com — fakeip=192.168.118.130 — interface=192.168.118.130
Now, one last step, let’s issue example.com request,
curl example.com
Let’s also navigate to example.com in browser,

we can see that we have successfully hijack the DNS.
Mitigations
There are some steps that we can take to improve DNS security to prevent DNS Hijacking Attacks :
1. Install Firewalls : To prevent attackers from installing fake resolvers in DNS and to legitimate resolvers, the IT team should place a firewall before resolvers.
2. Increase Restrictions : There should be limited access to organization’s DNS. IT team should enforce the physical security team, MFA, and a reliable firewall.
3. Prevent Cache Poisoning : To prevent website cache poisoning, implement randomize user identity, randomize server source ports, use upper and lower case in company’s domain name.
4. Fix Vulnerabilities : Identify any kind of vulnerabilities and patch them.
5. Zone Transfers : DNS zone records are sensitive files that contain data often by attackers. Attackers pose as slave name servers requesting for zone transfers and copy server zone records.
6. Up-to-date Technology : Users should frequently change their passwords, update anti-viruses, use VPNs.
7. Client Lock : Some DNS registrars use client locks to disable option to change DNS records unless request is made from approved IP address.
DNS Hijacking happens to website which are vulnerable. Despite all measures and efforts put in place by many business owners to avert DNS attacks and spoofing, hackers evolve by the day and develop new ways to infiltrate any vulnerable DNS of choice — stealing data and compromising networks. So it necessary to protect company’s website from DNS hijacking. Having security professionals finding bugs and IT team fix those bugs, is a good security practice that helps to prevent DNS Hijacking.
Needless to say, do not attempt this kind of attack on live systems, please.
Well, that’s all folks. I hope you enjoyed reading this blog. Stay safe, stay healthy. Until next time. Bye.
